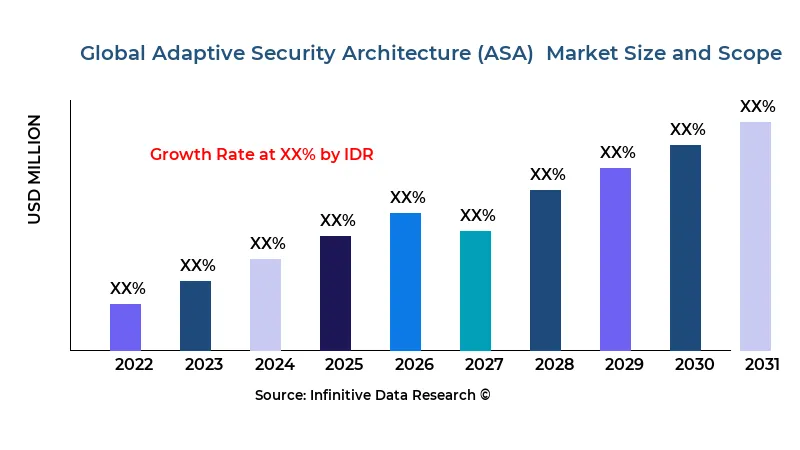
Adaptive Security Architecture (ASA) Market Growth CAGR Overview
According to research by Infinitive Data Research, the global Adaptive Security Architecture (ASA) Market size was valued at USD 16.6 Bln (billion) in 2024 and is Calculated to reach USD 31.6 Bln (billion) by the end of 2032, growing at an anticipated compound annual growth rate (CAGR) of 12.8% during the forecast period 2024 to 2032. This projected growth is driven by its increasing adoption across Telecommunications industries such as Government, Large Enterprise, Small and Medium EnterprisesThe cybersecurity landscape is evolving rapidly as digital transformation and cloud adoption accelerate. Organizations across industries are facing more sophisticated and persistent cyber threats. This has led to an increased demand for adaptive security architectures that not only protect but also dynamically adjust to the ever-changing threat environment. The need to secure diverse IT environments—from on-premise legacy systems to modern cloud infrastructures—has redefined security strategies, making adaptability a core requirement.
At the heart of these dynamics is the convergence of IT and operational technology. Enterprises are integrating multiple security controls into a unified platform, allowing for real‐time threat detection and response. This convergence supports the rapid identification of vulnerabilities and mitigates the impact of cyber incidents. Consequently, vendors are compelled to deliver comprehensive, flexible solutions that cater to an environment where threats are not static but continuously evolving.
Emerging technologies such as artificial intelligence (AI) and machine learning (ML) are also reshaping market dynamics. These technologies enable security solutions to predict, learn from, and adapt to new types of threats more effectively. As organizations increasingly adopt these advanced techniques, the market is witnessing a shift from reactive security measures to proactive and predictive security models, which are better aligned with today’s risk landscape.
Regulatory requirements and compliance mandates play a significant role as well. With governments and industry bodies enforcing stricter data protection laws and cybersecurity regulations, enterprises are under pressure to upgrade their security frameworks. This regulatory push is accelerating investments in adaptive security solutions that can evolve in tandem with new standards and compliance requirements, further intensifying market momentum.
Finally, the competitive landscape itself is a dynamic force driving market innovation. Increased investments in research and development (R&D), strategic alliances, and mergers and acquisitions have led to continuous improvements in product offerings. This competitive pressure encourages vendors to innovate rapidly, ensuring that their solutions remain effective against a backdrop of ever-escalating cyber threats and diversified attack vectors.
>>> Understand The Key Trends Shaping This Market:- Download PDF Sample
Adaptive Security Architecture Asa Market Growth Factors
Digital transformation is fundamentally altering the way businesses operate, leading to a significant expansion of the digital attack surface. The rapid integration of IoT devices, cloud services, and mobile technologies means that traditional security perimeters are no longer sufficient. Organizations must now rely on adaptive security architectures that can learn, evolve, and respond in real time to protect their critical assets, making digital transformation one of the primary growth drivers for the market.
The widespread adoption of cloud services and remote working models has added layers of complexity to the security landscape. As organizations transition to cloud-based infrastructures, they encounter new challenges such as data privacy, access control, and multi-tenant environments. These challenges create a pressing need for adaptive security solutions that can provide comprehensive coverage across diverse platforms, thereby fuelling significant market growth.
Regulatory pressures and compliance requirements continue to push companies toward enhanced security measures. Governments and regulatory bodies worldwide are mandating stricter standards for data protection and cybersecurity. Enterprises are compelled to invest in adaptive security frameworks that not only meet these regulatory demands but also offer the flexibility to adapt as standards evolve. This regulatory environment is a key catalyst for market expansion.
Technological advancements in AI, ML, and automation are rapidly transforming how security systems operate. By incorporating these advanced technologies, adaptive security solutions can analyze vast amounts of data, detect anomalies in real time, and predict potential breaches before they occur. The continuous improvement of these technologies is driving a shift from traditional static defenses to dynamic, data-driven security architectures, thereby boosting market growth.
Finally, heightened awareness and increased investment in cybersecurity by both public and private sectors have contributed to the market’s robust expansion. The rising frequency of cyber-attacks, data breaches, and ransomware incidents has underscored the critical need for advanced security measures. This has resulted in increased R&D spending and strategic initiatives by organizations to bolster their security postures, which in turn is spurring market growth.
Market Analysis By Competitors
- Cisco Systems
- Hewlett Packard Enterprise
- FireEye
- Dell EMC
- F-Secure
- Fortinet
- IBM
- Kaspersky Lab
- Microsoft
- Gartner
- Juniper Networks
- Brocade Communications Systems
- Check Point Software Technologies
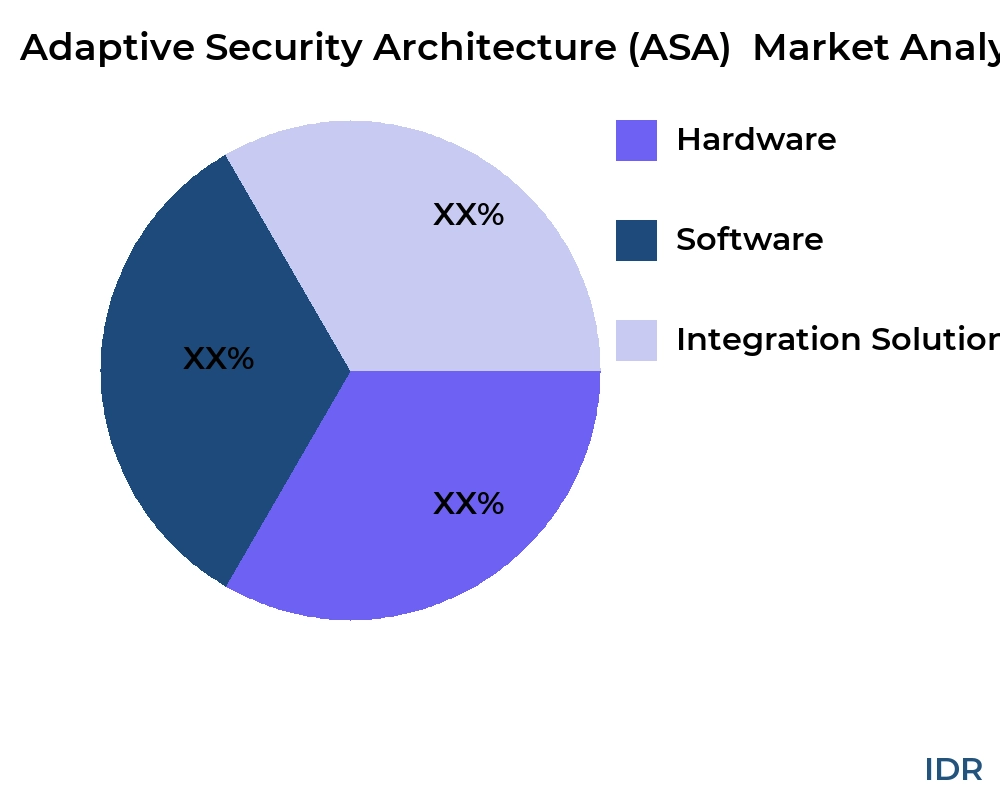
By Product Type
- Hardware
- Software
- Integration Solution
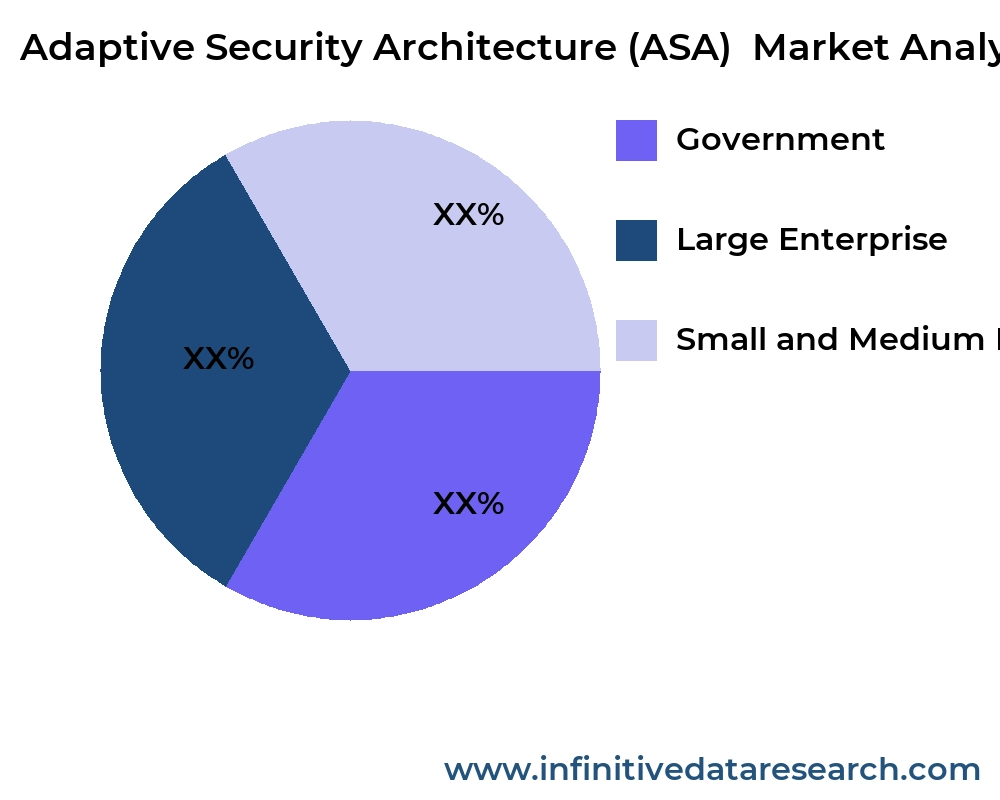
By Application
- Government
- Large Enterprise
- Small and Medium Enterprises
>>> Understand The Key Trends Shaping This Market:- Understand The Key Trends Shaping This Market:-
Adaptive Security Architecture Asa Market Segment Analysis
Distribution ChannelAdaptive security solutions are distributed through a variety of channels including direct sales, channel partners, system integrators, and managed security service providers. Each channel plays a crucial role in ensuring that the latest adaptive security technologies reach diverse customer segments—from large enterprises with complex IT infrastructures to small and medium-sized businesses seeking cost-effective protection. The trend toward hybrid sales models and digital distribution is also reshaping the channel strategy, as vendors strive to enhance their reach and offer seamless deployment experiences.
CompatibilityCompatibility is a critical factor in the adoption of adaptive security architectures. These solutions must integrate seamlessly with existing IT environments, including legacy systems, cloud platforms, and IoT devices. Market segmentation based on compatibility includes products that are engineered to work in heterogeneous environments versus those designed for new, cloud-native architectures. As enterprises look to modernize without disrupting existing operations, the ability of a security solution to offer backward compatibility while embracing future technologies is a significant driver of market preference.
Price RangeThe adaptive security architecture market caters to a wide range of budgets, resulting in segmentation by price. High-end, enterprise-grade solutions typically come with advanced analytics, real-time threat intelligence, and comprehensive support services, making them suitable for large organizations with complex security needs. In contrast, mid-range and cost-effective solutions are tailored for small to medium-sized businesses that require robust security without the heavy financial outlay. This price segmentation ensures that organizations of all sizes can access adaptive security solutions that meet their unique operational and financial constraints.
Product TypeThe product landscape within adaptive security architecture is diverse, encompassing software platforms, dedicated hardware appliances, and cloud-based services. Software solutions often emphasize real-time threat analysis and integration with existing IT ecosystems, while hardware appliances provide optimized performance and dedicated processing for security tasks. Cloud-based services, on the other hand, offer scalability, flexibility, and ease of deployment—features that are particularly attractive to rapidly growing organizations. Each product type addresses different operational requirements and budget considerations, allowing vendors to tailor their offerings to specific market segments.
| REPORT ATTRIBUTES | DETAILS |
|---|---|
| Study Period |
2019-2032 |
| Base Year |
2023 |
| Forecast Period |
2024-2032 |
| Historical Period |
2019-2022 |
| Unit |
Value (USD Billion) |
| Key Companies Profiled |
Cisco Systems, Hewlett Packard Enterprise, FireEye, Dell EMC, F-Secure, Fortinet, IBM, Kaspersky Lab, Microsoft, Gartner, Juniper Networks, Brocade Communications Systems, Check Point Software Technologies |
| Segments Covered |
By Product |
| Customization Scope |
Free report customization (equivalent to up to 3 analyst working days) with purchase. Addition or alteration to country, regional and segment scope |
>>> Overview of Market Analysis:- Download PDF Sample
Adaptive Security Architecture Asa Market Regional Analysis
In North America, the adaptive security architecture market is characterized by high technology adoption rates, a mature cybersecurity infrastructure, and stringent regulatory standards. Organizations in this region are early adopters of innovative security solutions and benefit from strong vendor support and comprehensive R&D investments. The advanced state of digital infrastructure in North America continues to drive robust market growth and serves as a benchmark for other regions.
Europe is witnessing a steady rise in demand for adaptive security solutions, driven by increasingly stringent data protection regulations and a proactive approach to cybersecurity. European enterprises, ranging from financial institutions to critical infrastructure providers, are investing heavily in adaptive security frameworks to ensure compliance and safeguard sensitive information. The focus on privacy and data integrity in Europe further propels the market, with vendors constantly adapting their offerings to meet local regulatory requirements.
The Asia-Pacific region is emerging as one of the fastest-growing markets for adaptive security architecture. Rapid digitalization, widespread adoption of cloud services, and a growing base of small and medium-sized enterprises are key factors driving demand. As governments and private enterprises invest significantly in modernizing IT infrastructures, the need for adaptive, scalable security solutions is becoming increasingly urgent, fostering strong market growth across countries in the region.
In Latin America, digital transformation is accelerating despite economic challenges, prompting organizations to enhance their cybersecurity frameworks. The adoption of adaptive security measures is gradually increasing as enterprises modernize their IT systems and recognize the importance of integrated threat management. Although the market here remains in a relatively nascent stage compared to more developed regions, steady growth is anticipated as awareness of cybersecurity risks spreads and investments in digital infrastructure increase.
The Middle East and Africa regions are also showing signs of significant growth, spurred by government initiatives and rising cybersecurity awareness. As digital economies expand and critical infrastructure becomes increasingly connected, the demand for adaptive security solutions is rising. Investments in cybersecurity are being bolstered by both public sector reforms and private sector initiatives aimed at protecting national assets and fostering a secure digital environment.
global Adaptive Security Architecture (ASA) market revenue (usd million) comparison by players 2024-2032
| Company/players | 2021 | 2022 | 2023 | 2024 | ... | (2032) |
|---|---|---|---|---|---|---|
| Cisco Systems | XX | XX | XX | XX | XX | XX |
| Hewlett Packard Enterprise | XX | XX | XX | XX | XX | XX |
| FireEye | XX | XX | XX | XX | XX | XX |
| Dell EMC | XX | XX | XX | XX | XX | XX |
| F-Secure | XX | XX | XX | XX | XX | XX |
| Fortinet | XX | XX | XX | XX | XX | XX |
| IBM | XX | XX | XX | XX | XX | XX |
| Kaspersky Lab | XX | XX | XX | XX | XX | XX |
| Microsoft | XX | XX | XX | XX | XX | XX |
| Gartner | XX | XX | XX | XX | XX | XX |
| Juniper Networks | XX | XX | XX | XX | XX | XX |
| Brocade Communications Systems | XX | XX | XX | XX | XX | XX |
| Check Point Software Technologies | XX | XX | XX | XX | XX | XX |
| Total | XX | XX | XX | XX | XX | XX |
global Adaptive Security Architecture (ASA) market revenue (usd million) comparison by product type 2024-2032
Product Type
2023
2024
...
2032
CAGR%(2024-32)
Hardware
XX
XX
XX
XX
XX
Software
XX
XX
XX
XX
XX
Integration Solution
XX
XX
XX
XX
XX
Total
XX
XX
XX
XX
XX
| Product Type | 2023 | 2024 | ... | 2032 | CAGR%(2024-32) |
|---|---|---|---|---|---|
| Hardware | XX | XX | XX | XX | XX |
| Software | XX | XX | XX | XX | XX |
| Integration Solution | XX | XX | XX | XX | XX |
| Total | XX | XX | XX | XX | XX |
global Adaptive Security Architecture (ASA) market revenue (usd million) comparison by application 2024-2032
Application
2023
2024
...
2032
CAGR%(2024-32)
Government
XX
XX
XX
XX
XX
Large Enterprise
XX
XX
XX
XX
XX
Small and Medium Enterprises
XX
XX
XX
XX
XX
Total
XX
XX
XX
XX
XX
| Application | 2023 | 2024 | ... | 2032 | CAGR%(2024-32) |
|---|---|---|---|---|---|
| Government | XX | XX | XX | XX | XX |
| Large Enterprise | XX | XX | XX | XX | XX |
| Small and Medium Enterprises | XX | XX | XX | XX | XX |
| Total | XX | XX | XX | XX | XX |
>>> Market Understand Through Graph And Chart:- Download PDF Sample
Adaptive Security Architecture Asa Market Competitive Insights
The competitive landscape in the adaptive security architecture market is both dynamic and diverse, featuring established global cybersecurity vendors alongside innovative startups. These companies are continuously enhancing their portfolios to address the rapidly changing threat environment. The battle for market leadership is marked by significant investments in R&D and strategic initiatives aimed at integrating next-generation technologies into their security offerings.
Innovation is a central pillar of competition, with vendors leveraging advanced technologies such as AI, ML, and automation to improve threat detection and response capabilities. This focus on technological advancement not only improves product performance but also drives differentiation among competitors. Companies that are quick to integrate emerging technologies into their solutions are better positioned to capture market share and set new industry standards.
Strategic partnerships, mergers, and acquisitions are common in this market, as organizations seek to broaden their capabilities and expand their geographic reach. These collaborations allow companies to offer comprehensive, end-to-end security solutions that address a wide range of customer needs. Consolidation trends within the market have led to the creation of more robust portfolios and have helped accelerate innovation, further intensifying competitive pressures.
Price competitiveness and service differentiation are crucial factors that influence customer decisions. Vendors are not only competing on the basis of technology but also on the strength of their support services, customized solution offerings, and flexible deployment models. This multifaceted approach to competition ensures that customers receive tailored solutions that meet their specific security requirements while maintaining cost efficiency.
Looking ahead, the competitive environment is expected to become even more intense as new entrants and disruptive technologies emerge. With ongoing consolidation and rapid technological innovation, established players are challenged to continually evolve their offerings. This dynamic competition benefits end-users, as it drives the continuous improvement of adaptive security solutions and promotes an environment of ongoing innovation and enhanced protection.
Adaptive Security Architecture Asa Market Competitors
United States
- Cisco Systems
- Palo Alto Networks
- Fortinet
- Check Point Software Technologies
- Juniper Networks
United Kingdom
- BT Security
- BAE Systems Applied Intelligence
- Darktrace
- Sophos
- Mimecast
Germany
- Avira
- G DATA Software
- Rohde & Schwarz Cybersecurity
- secunet Security Networks AG
- Infineon Technologies
France
- Thales Group
- Airbus CyberSecurity
- Stormshield
- Capgemini Cybersecurity
- [A leading French cybersecurity innovator]
Canada
- Blackberry
- Herjavec Group
- CGI Cybersecurity
- Absolute Software
- eSentire
Australia
- Telstra
- Tesserent
- CyberCX
- Optus Cyber Security
- Secure Enterprise
Japan
- Trend Micro
- NEC Corporation (Security Division)
- Hitachi Systems Security
- Fujitsu Cyber Security
- NTT Security Japan
India
- Quick Heal Technologies
- Paladion Networks
- Sify Technologies Cybersecurity
- Wipro Cybersecurity
- Tata Consultancy Services Cyber Security
Brazil
- Stefanini
- Tempest Security Intelligence
- Sonda IT
- Módulo Security
- Indra Brazil
Russia
- Kaspersky Lab
- Group-IB
- Positive Technologies
- InfoWatch
- Rostelecom Cyber Division
China
- Qihoo 360
- Huawei Cyber Security
- NSFOCUS
- DBAPPSecurity
- Venustech
South Korea
- AhnLab
- Samsung SDS Cybersecurity
- SK Infosec
- Hancom Secure
- LG CNS Cyber Security
Italy
- Leonardo S.p.A.
- Olivetti Cyber Security
- Cybertech Italia
- Noovle Cyber Defense
- BT Italia Security
Spain
- Indra Sistemas
- S21sec
- Panda Security
- GMV Cybersecurity
- Telefónica Tech
Netherlands
- Fox-IT
- SecureLink Netherlands
- Ordina Cyber Security
- Computest
- KPN Security
Sweden
- Ericsson Security
- Sectra
- Clavister
- Advenica
- SafeGuard Sweden
Switzerland
- Kudelski Security
- Swisscom Cyber Security
- ELCA Cyber
- Adnovum Cyber Defense
- Securitas Switzerland
Singapore
- ST Engineering Cybersecurity
- Singtel Cyber Security
- SecureAge Technologies
- Horangi Cyber Security
- Quann
Israel
- Check Point Software Technologies
- CyberArk
- Radware
- Imperva
- Guardicore
United Arab Emirates
- DarkMatter UAE
- Injazat
- Etisalat Cyber Security
- Emirates Cyber Defense
- CyberGate UAE
Mexico
- KIO Networks Cybersecurity
- Telmex Cyber Security
- Softtek Cyber Solutions
- Neoris Cyber Defense
- Cipher Mexico
South Africa
- Dimension Data Cyber Security
- EOH Cyber
- Bytes Technology Group Cyber Division
- Datacentrix Cyber Security
- Adapt IT Cyber Solutions
New Zealand
- Datacom Group Cyber Security
- Spark New Zealand Cyber Defense
- Orion Health Cyber
- Cerner New Zealand Cyber
- Xero Cyber Solutions
Belgium
- Proximus Cyber Security
- Agfa Cyber Defense
- Barco Secure
- EVS Cyber Solutions
- SecureLink Belgium
Austria
- A1 Telekom Cyber Security
- Kapsch Cyber Solutions
- Frequentis Cyber Defense
- Red Bull Cyber
- TÜV Austria Cyber
Denmark
- Netcompany Cyber Security
- NNIT Cyber
- CSIS Security
- KMD Cyber Security
- Trifork Cyber Solutions
Norway
- Telenor Cyber
- Visma Cyber Security
- Basefarm Cyber Defense
- Computas Cyber
- Capgemini Norway Cyber
Finland
- F‑Secure
- Nokia Cyber Security
- SSH Communications Security
- Nixu
- Siili Cyber Solutions
Poland
- Comarch Cyber Security
- Asseco Cyber Security
- Exatel Cyber Solutions
- Sygnity Cyber Defense
- Netia Cyber Security
Turkey
- Havelsan Cyber Security
- Turkcell Cyber Defense
- ASELSAN Cyber
- STM Cyber Solutions
- Bimser Cyber
Adaptive Security Architecture Asa Market Top Competitors
1. Cisco SystemsCisco Systems stands at the forefront of the adaptive security architecture market with a comprehensive portfolio that integrates advanced networking and cybersecurity solutions. Renowned for its innovation and global reach, Cisco leverages deep R&D expertise to continuously upgrade its security offerings. Its integrated platforms are designed to offer real‑time threat detection and automated responses, making it a trusted partner for enterprises worldwide. Cisco’s strategic alliances and robust customer base underscore its dominant market position and its pivotal role in shaping adaptive security trends.
2. Palo Alto NetworksPalo Alto Networks is widely recognized as a leading innovator in the cybersecurity space, particularly in the realm of adaptive security. The company’s next-generation security platforms incorporate machine learning and automation to deliver proactive threat prevention and real‑time risk mitigation. With a strong emphasis on integrating network, cloud, and endpoint security, Palo Alto Networks has solidified its reputation as a market leader. Its forward-thinking strategy and continuous product enhancements position the company at the cutting edge of cybersecurity innovation.
3. FortinetFortinet has earned a solid reputation as a major player in adaptive security, driven largely by its high-performance security fabric and FortiGate firewall solutions. The company’s approach centers on integrating advanced threat intelligence with scalable, flexible security measures that adapt to modern enterprise needs. Fortinet’s consistent investments in R&D and its focus on delivering robust, cost‐effective solutions across various market segments have helped it maintain a competitive edge in a rapidly evolving cybersecurity environment.
4. Check Point Software TechnologiesWith a long-standing history in cybersecurity, Check Point Software Technologies has evolved its offerings to meet the demands of adaptive security. Its comprehensive security platforms emphasize real‑time threat intelligence, multi-layered defense, and seamless integration across various IT environments. Check Point’s commitment to innovation and its rigorous approach to risk management have made it a trusted name among global enterprises. The company continues to lead by adapting its solutions to meet the sophisticated demands of today’s dynamic threat landscape.
5. Juniper NetworksOriginally celebrated for its networking innovations, Juniper Networks has successfully expanded into the cybersecurity arena by integrating adaptive security features into its robust network infrastructure. By leveraging its extensive expertise in high-speed routing and switching, Juniper offers scalable security solutions tailored for the complexities of modern digital environments. Its commitment to innovation, bolstered by strategic partnerships and a global footprint, has positioned Juniper Networks as a significant contributor to the adaptive security market.
6. Trend MicroTrend Micro is a well-established name in the cybersecurity world, with a strong emphasis on adaptive security solutions for cloud, endpoint, and hybrid environments. The company’s platforms leverage cutting-edge analytics and machine learning to detect, analyze, and neutralize emerging threats in real time. Trend Micro’s continuous focus on enhancing threat intelligence and its proven track record in protecting enterprise data contribute to its status as one of the industry’s most trusted and innovative competitors.
7. IBM SecurityIBM Security brings to the market a unique blend of advanced analytics, artificial intelligence, and deep industry expertise. Its adaptive security solutions integrate seamlessly with an organization’s broader IT ecosystem, allowing for the proactive detection and rapid mitigation of complex threats. With a strong emphasis on data-driven insights and comprehensive risk management, IBM Security has established itself as a key player in enterprise security. Its global presence and commitment to innovation further reinforce its leadership in adaptive security architectures.
8. McAfeeMcAfee’s extensive portfolio in cybersecurity includes robust adaptive security solutions that are designed to offer integrated, real-time protection across endpoints, networks, and cloud environments. The company’s focus on leveraging data analytics and machine learning for threat detection and response has enabled it to maintain a significant market presence. McAfee’s dedication to continuous improvement and customer-centric innovation has solidified its position as a reliable and forward-thinking competitor in the adaptive security market.
9. Broadcom (Symantec Enterprise Division)Broadcom’s enterprise security division, which evolved from the renowned Symantec brand, continues to play a major role in adaptive security. The division offers comprehensive solutions that blend robust data protection with advanced threat intelligence and real‑time analytics. Its integrated approach and global reach have allowed Broadcom to sustain a strong competitive position in the market. With continuous investments in technology and strategic market initiatives, Broadcom remains a formidable force in driving adaptive security innovation.
10. RSA SecurityRSA Security is highly respected for its sophisticated risk management and security analytics solutions, which are integral to its adaptive security architecture. Specializing in identity and access management as well as advanced threat detection, RSA has carved out a niche by offering solutions that adapt to complex security environments. The company’s focus on integrating advanced analytics and ensuring robust protection against emerging threats has cemented its reputation as a trusted and influential player. RSA’s ongoing commitment to innovation and collaborative partnerships continues to reinforce its competitive position in the cybersecurity landscape.
The report provides a detailed analysis of the Adaptive Security Architecture (ASA) market across various regions, highlighting the unique market dynamics and growth opportunities in each region.
- US
- Canada
- Mexico
- UK
- Germany
- France
- Italy
- Russia
- Spain
- Switzerland
- Austria
- Belgium
- Rest of Europe
- China
- Japan
- South Korea
- Indonesia
- Vietnam
- Philippines
- Australia
- Thailand
- Singapore
- Rest of APAC
- UAE
- Saudi Arabia
- Egypt
- South Africa
- Israel
- Rest of MEA
- Brazil
- Argentina
- Rest of Latin America
>>> Need A Different Region Or Segment? Download PDF Sample
Key Takeaways
- The global Adaptive Security Architecture (ASA) market is expected to grow significantly from 2024 to 2032, driven by technological advancements, increasing demand, and government investments in urbanization.
- The market is characterized by a diverse range of manufacturers, product types, and applications, catering to different consumer needs and preferences.
- Regional insights highlight the unique market dynamics and growth opportunities in various regions, including North America, Europe, Asia-Pacific, Latin America, and the Middle East & Africa.
- The competitive landscape features key players who have created a dynamic and diverse market environment through collaborations, mergers and acquisitions, and innovative product developments.
- Market trends such as technological advancements, sustainability, customization, and digital transformation are shaping the growth and development of the Adaptive Security Architecture (ASA) market.
- Despite the positive outlook, the market faces challenges such as regulatory compliance, high initial investment costs, and economic uncertainties.
- The report provides comprehensive coverage of market size, market share, growth factors, and strategic insights to help businesses navigate the dynamic Adaptive Security Architecture (ASA) market and achieve long-term success.
By leveraging the information provided in this report, businesses can develop effective strategies, address market challenges, and capitalize on growth opportunities to ensure sustainable growth and long-term success in the global Adaptive Security Architecture (ASA) market.
- Introduction
- Objectives of the Study
- Market Definition
- Research Scope
- Currency
- Key Target Audience
- Research Methodology and Assumptions
- Executive Summary
- Premium Insights
- Porter’s Five Forces Analysis
- Value Chain Analysis
- Top Investment Pockets
- Industry Trends
- Market Dynamics
- Market Evaluation
- Drivers
- Restraints
- Opportunities
- Challenges
- Global Adaptive Security Architecture (ASA) Market Analysis and Projection, By Companies
- Segment Overview
- Cisco Systems
- Hewlett Packard Enterprise
- FireEye
- Dell EMC
- F-Secure
- Fortinet
- IBM
- Kaspersky Lab
- Microsoft
- Gartner
- Juniper Networks
- Brocade Communications Systems
- Check Point Software Technologies
- Global Adaptive Security Architecture (ASA) Market Analysis and Projection, By Type
- Segment Overview
- Hardware
- Software
- Integration Solution
- Global Adaptive Security Architecture (ASA) Market Analysis and Projection, By Application
- Segment Overview
- Government
- Large Enterprise
- Small and Medium Enterprises
- Global Adaptive Security Architecture (ASA) Market Analysis and Projection, By Regional Analysis
- North America
- US
- Canada
- Mexico
- Europe
- UK
- Germany
- France
- Italy
- Russia
- Spain
- Switzerland
- Austria
- Belgium
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- Indonesia
- Vietnam
- Philippines
- Australia
- Thailand
- Singapore
- Rest of APAC
- Middle East
- UAE
- Saudi Arabia
- Egypt
- South Africa
- Israel
- Rest of MEA
- Latin America
- Brazil
- Argentina
- Rest of Latin America
- Global Adaptive Security Architecture (ASA) Market-Competitive Landscape
- Overview
- Market Share of Key Players in the Adaptive Security Architecture (ASA) Market
- Global Company Market Share
- North America Company Market Share
- Europe Company Market Share
- APAC Company Market Share
- Competitive Situations and Trends
- Coverage Launches and Developments
- Partnerships, Collaborations, and Agreements
- Mergers & Acquisitions
- Expansions
- Company Profiles
- Cisco Systems
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Hewlett Packard Enterprise
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- FireEye
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Dell EMC
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- F-Secure
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Fortinet
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- IBM
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Kaspersky Lab
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Microsoft
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Gartner
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Juniper Networks
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Brocade Communications Systems
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
- Check Point Software Technologies
- Business Overview
- Company Snapshot
- Company Market Share Analysis
- Company Coverage Portfolio
- Recent Developments
- SWOT Analysis
List of Table
- Drivers of Global Adaptive Security Architecture (ASA) Market: Impact Analysis
- Restraints of Global Adaptive Security Architecture (ASA) Market: Impact Analysis
- Global Adaptive Security Architecture (ASA) Market, By Technology, 2023-2032(USD Billion)
- global Hardware, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Software, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Integration Solution, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Government, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Large Enterprise, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Small and Medium Enterprises, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
List of Figures
- Global Adaptive Security Architecture (ASA) Market Segmentation
- Adaptive Security Architecture (ASA) Market: Research Methodology
- Market Size Estimation Methodology: Bottom-Up Approach
- Market Size Estimation Methodology: Top-down Approach
- Data Triangulation
- Porter’s Five Forces Analysis
- Value Chain Analysis
- Top investment pocket in the Adaptive Security Architecture (ASA) Market
- Top Winning Strategies, 2023-2032
- Top Winning Strategies, By Development, 2023-2032(%)
- Top Winning Strategies, By Company, 2023-2032
- Moderate Bargaining power of Buyers
- Moderate Bargaining power of Suppliers
- Moderate Bargaining power of New Entrants
- Low threat of Substitution
- High Competitive Rivalry
- Restraint and Drivers: Adaptive Security Architecture (ASA) Market
- Adaptive Security Architecture (ASA) Market Segmentation, By Technology
- Adaptive Security Architecture (ASA) Market For Live Attenuated, By Region, 2023-2033 ($ Billion)
- Global Adaptive Security Architecture (ASA) Market, By Technology, 2023-2032(USD Billion)
- global Hardware, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Software, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Integration Solution, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Government, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Large Enterprise, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- global Small and Medium Enterprises, Adaptive Security Architecture (ASA) Market, By Region, 2023-2032(USD Billion)
- Cisco Systems: Net Sales, 2023-2033 ($ Billion)
- Cisco Systems: Revenue Share, By Segment, 2023 (%)
- Cisco Systems: Revenue Share, By Region, 2023 (%)
- Hewlett Packard Enterprise: Net Sales, 2023-2033 ($ Billion)
- Hewlett Packard Enterprise: Revenue Share, By Segment, 2023 (%)
- Hewlett Packard Enterprise: Revenue Share, By Region, 2023 (%)
- FireEye: Net Sales, 2023-2033 ($ Billion)
- FireEye: Revenue Share, By Segment, 2023 (%)
- FireEye: Revenue Share, By Region, 2023 (%)
- Dell EMC: Net Sales, 2023-2033 ($ Billion)
- Dell EMC: Revenue Share, By Segment, 2023 (%)
- Dell EMC: Revenue Share, By Region, 2023 (%)
- F-Secure: Net Sales, 2023-2033 ($ Billion)
- F-Secure: Revenue Share, By Segment, 2023 (%)
- F-Secure: Revenue Share, By Region, 2023 (%)
- Fortinet: Net Sales, 2023-2033 ($ Billion)
- Fortinet: Revenue Share, By Segment, 2023 (%)
- Fortinet: Revenue Share, By Region, 2023 (%)
- IBM: Net Sales, 2023-2033 ($ Billion)
- IBM: Revenue Share, By Segment, 2023 (%)
- IBM: Revenue Share, By Region, 2023 (%)
- Kaspersky Lab: Net Sales, 2023-2033 ($ Billion)
- Kaspersky Lab: Revenue Share, By Segment, 2023 (%)
- Kaspersky Lab: Revenue Share, By Region, 2023 (%)
- Microsoft: Net Sales, 2023-2033 ($ Billion)
- Microsoft: Revenue Share, By Segment, 2023 (%)
- Microsoft: Revenue Share, By Region, 2023 (%)
- Gartner: Net Sales, 2023-2033 ($ Billion)
- Gartner: Revenue Share, By Segment, 2023 (%)
- Gartner: Revenue Share, By Region, 2023 (%)
- Juniper Networks: Net Sales, 2023-2033 ($ Billion)
- Juniper Networks: Revenue Share, By Segment, 2023 (%)
- Juniper Networks: Revenue Share, By Region, 2023 (%)
- Brocade Communications Systems: Net Sales, 2023-2033 ($ Billion)
- Brocade Communications Systems: Revenue Share, By Segment, 2023 (%)
- Brocade Communications Systems: Revenue Share, By Region, 2023 (%)
- Check Point Software Technologies: Net Sales, 2023-2033 ($ Billion)
- Check Point Software Technologies: Revenue Share, By Segment, 2023 (%)
- Check Point Software Technologies: Revenue Share, By Region, 2023 (%)
Infinitive Data Research provides comprehensive market research, offering in-depth market analysis to help companies understand their target market and industry competition. This research predicts the market acceptance of your brand and products, ensuring informed decision-making for business success.
Competitor Analysis in the Adaptive Security Architecture (ASA) Industry
Conducting a competitor analysis involves identifying competitors within the Adaptive Security Architecture (ASA) industry and studying their various marketing strategies. This comparative data allows you to assess your company's strengths and weaknesses relative to competitors, providing insights to enhance your market position.
Importance of Continuous Market Research
Consistently conducting market research is essential for minimizing risk at every stage of business operations. Adaptive Security Architecture (ASA) market research enables you to collect qualitative and quantitative data, which, when properly analyzed, leads to wise decisions that align with user and customer needs. Below are some crucial lessons learned through the Adaptive Security Architecture (ASA) market research process:

Key Dimensions of Adaptive Security Architecture (ASA) Market Analysis
- Trend and Pattern Identification: Analyzing data to spot market trends and patterns.
- Pricing Analysis: Assessing keyword pricing strategies.
- Actionable Insights: Implementing insights derived from data analysis.
- Market Potential: Evaluating the potential of the Adaptive Security Architecture (ASA) market.
- Competitor Analysis: Studying competitors' strategies and performance.
- Location Analysis: Assessing optimal locations for market penetration.
- Distribution Channels Analysis: Evaluating the effectiveness of distribution channels.
- Market Size and Growth Rate: Measuring market size and growth potential.
- Market Profitability: Assessing profitability prospects.
- Key Success Factors: Identifying critical factors for success.
- Cost Structure: Understanding the cost structure within the Adaptive Security Architecture (ASA) industry.
Target Audience for the Report
This report is valuable for a diverse audience, including:
- Adaptive Security Architecture (ASA) Market Manufacturers: To understand market dynamics and enhance production strategies.
- Investors and Financing Companies: To assess investment opportunities and risks.
- Adaptive Security Architecture (ASA) Market Suppliers: To identify market demands and supply chain efficiencies.
Necessity of the Report
Making Crucial Business Decisions
Understanding the Adaptive Security Architecture (ASA) market, competition, and industry landscape is vital for making informed business decisions. Without current and relevant market research, decisions may be based on outdated or irrelevant information, potentially harming the business.
Securing Investment Funds
Attracting investors requires demonstrating thorough market research. Investors need assurance that you understand the sector, current and potential competition, and whether your idea addresses a market need.
Identifying New Business Opportunities
Adaptive Security Architecture (ASA) market research goes beyond understanding trends and consumer behavior. It identifies new revenue streams and opportunities for business pivots. These insights can lead to strategic changes in the business model, promoting growth and adapting to market challenges.
Avoiding Business Failures
Market research also plays a crucial role in risk mitigation. It can reveal when not to pursue certain actions, saving the company from potential losses in revenue, brand image, and more. This proactive approach is often overlooked but is essential for long-term success.
Conclusion
Infinitive Data Research's comprehensive Adaptive Security Architecture (ASA) market research provides critical insights for making solid business decisions, securing investments, identifying new opportunities, and avoiding potential failures. Understanding market dynamics through continuous research ensures your company remains competitive and thrives in the Adaptive Security Architecture (ASA) industry.